While I'm not convinced that encrypting everything by default is
necessarily a good idea, it is certainly true that encryption has its
uses. Unfortunately, for the longest time getting an SSL certificate
from a CA was quite a hassle -- and then I'm not even mentioning the
fact that it would cost money, too. In that light, the letsencrypt
project is a useful alternative: rather than having to dabble with
emails or webforms, letsencrypt does everything by way of a few scripts.
Also, the letsencrypt CA is free to use, in contrast to many other
certificate authorities.
Of course, once you start scripting, it's easy to overdo it. When you go
to the letsencrypt website and try to install their stuff, they point
you to a "letsencrypt-auto" thing, which starts installing a python
virtualenv and loads of other crap, just so we can talk to a server
and get a certificate properly signed. I'm sure that makes sense for
some people, and I'm also sure it makes some things significantly
easier, but honestly, I think it's a bit overkill. Luckily, there is
also a regular
letsencrypt script that doesn't do all the
virtualenv
stuff, and which is
already packaged for
Debian, so
installing that gets us rid of the overkill bits. It's not in stable,
but it
is an arch:all package. Unfortunately, not all dependencies are
available in Jessie, but backporting it turned out to be not too complicated.
Once the client is installed, you need to get it to obtain a
certificate, and you need to have the certificate be activated for your
webserver. By default, the letsencrypt client will update your server
configuration for you, and run a temporary webserver, and do a whole lot
of other things that I would rather not see it do. The good news,
though, is that you can switch all that off. If you're willing to let it
write a few files to your DocumentRoot, it can do the whole thing
without any change to your system:
letsencrypt certonly -m <your mailaddress> --accept-tos --webroot -w \
/path/to/DocumentRoot -d example.com -d www.example.com
In that command, the
-m option (with mail address) and the
--accept-tos option are only required the first time you ever run
letsencrypt. Doing so creates an account for you at letsencrypt.org,
without which you cannot get any certificates. The
--accept-tos
option specifies that you accept
their terms of
service, which you might want to
read first before blindly accepting.
If all goes well,
letsencrypt will tell you that it wrote your account
information and some certificates somewhere under
/etc/letsencrypt.
All that's left is to update your webserver configuration so that the
certificates are actually used. No, I won't tell you how that's done --
if you need that information, it's probably better if you just use the
apache or nginx plugin of
letsencrypt, which updates your webserver's
configuration automatically. But if you already know how to do so, and
prefer to maintain your configuration by yourself, then it's good to
know that it is at least possible.
Since we specified two
-d parameters, the certificate you get from the
letsencrypt CA will have subjectAlternativeName fields, allowing you to
use them for more than one domain name. I specified
example.com
and
www.example.com as the valid names, but there is nothing in
letsencrypt requiring that the domain names you specify share a
suffix; so yes, it is certainly possible to have multiple domains on a
single certificate, if you want that.
Finally, you need to ensure that your certificates are renewed before
they expire. The easiest way to do that is to add a cronjob, which runs
letsencrypt again; only this time, you'll need slightly different
options:
letsencrypt certonly --renew-by-default --webroot -w \
/path/to/DocumentRoot -d domain.name.tld -d www.domain.name.tld
The
--renew-by-default option tells
letsencrypt that you want to
renew your certificates, not create new ones. If you specify this, the
old certificate will be revoked, and a new one will be generated, again
with three months validity. The symlinks under
/etc/letsencrypt/live
will be updated, so if your webserver's configuration uses those as the
path to your certificates, you don't need to update any configuration
files (although you may need to restart your webserver). You'll also
notice that the
-m and
--accept-tos options are not specified this
time around; this is because those are only required when you want to
create an account -- once that step has been taken,
letsencrypt will
read the necessary information from its configuration files (and
creating a new account for every renewal is just silly).
With that, you now have a working, browser-trusted, certificate.
Update: fix mistake about installing on Jessie. It's possible (I've
done so), but it's been a while and I forgot that I had to recompile
several of
letsencrypt's dependencies in order for it to be
installable.
 Due to some technical issues, it took a slight bit longer than I'd
originally expected; but the first four videos of the currently running
DebConf 17 conference are
available.
Filenames are based on the talk title, so that should be reasonably easy
to understand. I will probably add an RSS feed (like we've done for
DebConf
16)
to that place some time soon as well, but code for that still needs to
be written.
Meanwhile, we're a bit behind on the reviewing front, with (currently)
34 talks still needing review. If you're interested in helping out,
please join the #debconf-video channel on OFTC and ask what you can do.
This is something which you can do from home if you're interested, so
don't be shy! We'd be happy for your help.
Due to some technical issues, it took a slight bit longer than I'd
originally expected; but the first four videos of the currently running
DebConf 17 conference are
available.
Filenames are based on the talk title, so that should be reasonably easy
to understand. I will probably add an RSS feed (like we've done for
DebConf
16)
to that place some time soon as well, but code for that still needs to
be written.
Meanwhile, we're a bit behind on the reviewing front, with (currently)
34 talks still needing review. If you're interested in helping out,
please join the #debconf-video channel on OFTC and ask what you can do.
This is something which you can do from home if you're interested, so
don't be shy! We'd be happy for your help.
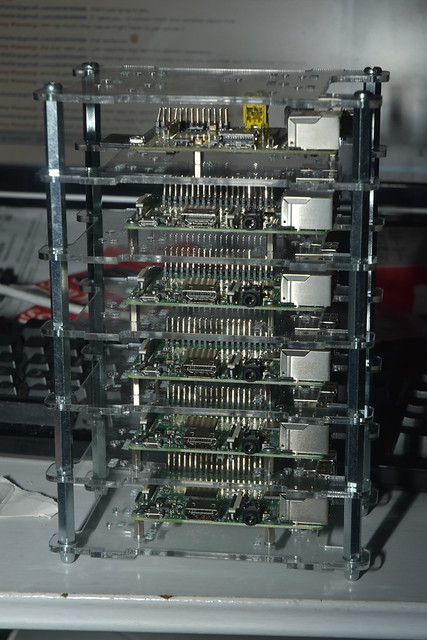
 About a year ago I bought a new workstation computer for myself at
home. It s a
About a year ago I bought a new workstation computer for myself at
home. It s a  If you write a list of things not to do, then by implication (because
you didn't mention them), the things in the gray area are okay. This is
especially problematic when it comes to things that are borderline
blacklisted behaviour (or that should be blacklisted but aren't, because
your list is incomplete -- see above). In such a situation, you're
dealing with people who are jerks but can argue about it because your
definition of jerk didn't cover teir behaviour. Because they're jerks,
you can be sure they'll do everything in their power to waste your time
about it, rather than improving their behaviour.
In contrast, if you write a list of things that you want people to do,
then by implication (because you didn't mention it), the things in the
gray area are not okay. If someone slips and does something in that
gray area anyway, then that probably means they're doing something
borderline not-whitelisted, which would be mildly annoying but doesn't
make them jerks. If you point that out to them, they might go "oh,
right, didn't think of it that way, sorry, will aspire to be better next
time". Additionally, the actual jerks and trolls will have been given
less tools to argue about borderline violations (because the border of
your code of conduct is far, far away from jerky behaviour), so less
time is wasted for those of your community who have to police it (yay!).
In theory, the result of a whitelist is a community of people who aspire
to be nice people, rather than a community of people who simply aspire
to be "not jerks". I know which kind of community I prefer.
If you write a list of things not to do, then by implication (because
you didn't mention them), the things in the gray area are okay. This is
especially problematic when it comes to things that are borderline
blacklisted behaviour (or that should be blacklisted but aren't, because
your list is incomplete -- see above). In such a situation, you're
dealing with people who are jerks but can argue about it because your
definition of jerk didn't cover teir behaviour. Because they're jerks,
you can be sure they'll do everything in their power to waste your time
about it, rather than improving their behaviour.
In contrast, if you write a list of things that you want people to do,
then by implication (because you didn't mention it), the things in the
gray area are not okay. If someone slips and does something in that
gray area anyway, then that probably means they're doing something
borderline not-whitelisted, which would be mildly annoying but doesn't
make them jerks. If you point that out to them, they might go "oh,
right, didn't think of it that way, sorry, will aspire to be better next
time". Additionally, the actual jerks and trolls will have been given
less tools to argue about borderline violations (because the border of
your code of conduct is far, far away from jerky behaviour), so less
time is wasted for those of your community who have to police it (yay!).
In theory, the result of a whitelist is a community of people who aspire
to be nice people, rather than a community of people who simply aspire
to be "not jerks". I know which kind of community I prefer.